Communications and Marketing
Online security: passwords are easy targets
More and more often, people are attempting to intercept or guess others’ passwords and exploit them for criminal ends, usually resulting in financial loss for the users. Stephan Wiefling is a doctoral student and member of Prof. Luigi Lo Iacono’s Data and Application Security (DAS) Group, which is part of the Department of Computer Science at Hochschule Bonn-Rhein-Sieg. He is working on methods that allow legitimate users to be identified as such when they log in while frustrating fraudsters’ intentions.
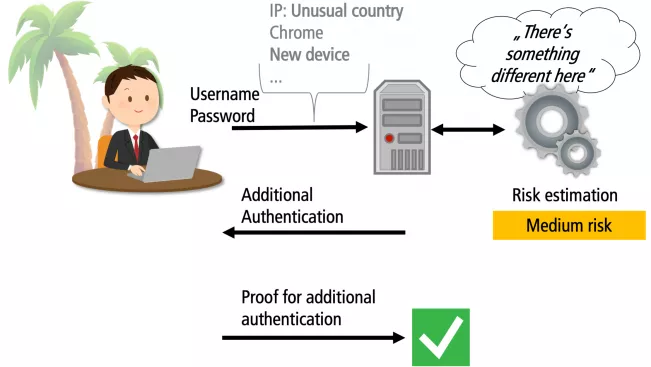
"It’s about risk-based authentication, or RBA for short," says Wiefling. According to this principle, he says, a website will accept a user name and password as long as the system does not detect anything suspicious. Only if the user’s behaviour gives it reason to doubt that a legitimate person is attempting to log in will it request a second form of authentication. Any non-standard behaviour will be deemed suspicious. If, for instance, someone is using a device for the first time, logging in from an unusual location and possibly at an even more unusual time, the system will interpret this as non-standard behaviour and request confirmation that the login is legitimate.
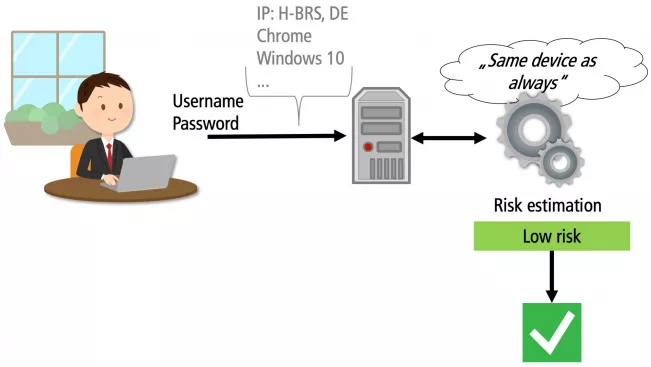
RBA is thus convenient for users in that they only need to enter their password once to be accepted by the website unless anything unusual happens. This has also been confirmed in a lab study involving nearly 70 users: according to Wiefling, they felt that RBA was much more secure than a purely password-based authentication process. Specifically, they had an overwhelming preference for RBA for websites that hold personal data such as social media services and online shopping.
That is not all, however: in his research project, Wiefling is also comparing RBA with two-factor authentication (2FA), which always requires users to verify their identity using two different characteristics, such as a password and unique PIN, in order to be let in by the system. Although RBA enjoys a much higher level of acceptance than 2FA and offers the same feeling of security, there is an exception, Wiefling says: two-factor authentication is still the favoured method for websites with very high security requirements, such as online banking.
Password security and guesswork
But how do cybercriminals get hold of passwords in the first place, and what techniques do they use? What characteristics should secure passwords have?
Stephan Wiefling outlines the two critical situations. The first includes major data breaches, where customer data including their passwords is stolen, as has happened in the past at LinkedIn, Adobe and MySpace. The hackers then use automated processes to see if these combinations of e-mail addresses and passwords also work on other websites. This technique, known as “credential stuffing”, is registered 250 million times a day by the online service provider Akamai alone.

The second, increasingly sophisticated, method involves simply guessing the passwords – with astounding success. Says Wiefling: "The success rate is as high as 70 per cent, even after fewer than 100 guesses." The guesswork method is based on assumptions and available data. A fraudster gathers information on their target, such as the names and dates of birth of family members and maybe even pre-discovered passwords or the name of their pet. Their computer then uses statistical assumptions to come up with a list of potential passwords deemed to be the most likely. "After all, we’re only human and find it hard to remember cryptic combinations of letters, numbers and characters," says Wiefling, explaining the alarming success of the method, which was scientifically described as long ago as 2016.
To create his passwords, Wiefling uses a password manager, a service offered by some Internet browsers. He also recommends not using the same password for multiple online services, adding that not every password needs to be fiendishly complicated. In his view, a longer phrase like "I often like working Mondays" will generally be more secure than shorter combinations of characters that are hard to remember, such as "$Le90pch". This gives him a whole series of passwords, which he stores in an online safe, where they are automatically encrypted. Users then only need to remember a single password, which opens the safe and decrypts the individual passwords.
Positive feedback from IT security experts
During his research, doctoral student Wiefling has already published a number of papers and articles containing results that have attracted considerable attention in the industry. The world-renowned IT security expert Bruce Schneier, for instance, has recommended Wiefling’s latest study in his blog. The RBA developers at Google have also been very impressed with his work. This makes him confident that his findings could lead to RBA being used more widely. "As a result, even more users could enjoy the benefits of this technology," Wiefling says.
At H-BRS, BSc Computer Science students can already choose a specialist information security option, and a “Cybersecurity and Privacy” course is set to launch in the 2021/22 winter semester.